Most businesses install CCTV not just for recording but to actively prevent crime and protect people. Studies show that visible surveillance reduces property crime rates by up to 50 percent, making it a powerful tool for safety. With rising security threats and tighter regulations, understanding how modern CCTV monitoring works can shape smarter, safer environments. This guide breaks down the systems, benefits, and legal side of surveillance so you can secure your property with confidence.
Table of Contents
- Defining CCTV Monitoring and Its Purpose
- Types of CCTV Systems and Monitoring Methods
- How CCTV Monitoring Works in Practice
- Legal Responsibilities and Data Protection UK
- Common Mistakes and Security Vulnerabilities
Key Takeaways
| Point | Details |
|---|---|
| CCTV Enhances Security | CCTV monitoring goes beyond recording; it actively deters crime and provides critical evidence for investigations. |
| Diverse System Types | Various CCTV systems, including analogue, digital, and cloud-based, cater to different security needs and operational environments. |
 |
|
| Legal Compliance is Essential | Organizations must navigate complex data protection laws and understand their legal responsibilities to ensure responsible CCTV operation. |
| Integration and Maintenance are Key | Effective security relies on integrating CCTV with other measures and maintaining the system to avoid vulnerabilities and maximize effectiveness. |
Defining CCTV Monitoring and Its Purpose
CCTV monitoring represents a sophisticated security strategy that transforms passive visual recording into an active protective mechanism. According to the National Protective Security Authority, CCTV is fundamentally a system designed for surveillance and security purposes, capturing and recording images that can deter or detect potential criminal activities.
At its core, CCTV monitoring goes far beyond simple video recording. The College of Policing highlights that these surveillance cameras serve multiple critical functions: enhancing security personnel capabilities, preventing personal and property crime, and managing public order scenarios. This isn’t just about capturing footage – it’s about creating a comprehensive security ecosystem that provides real-time awareness and potential intervention.
Key purposes of CCTV monitoring include:
- Deterring potential criminal activities through visible surveillance
- Providing visual evidence for investigations if incidents occur
- Monitoring high-risk or vulnerable areas continuously
- Supporting law enforcement with actionable visual intelligence
- Offering a cost-effective alternative to constant human security presence
While CCTV cannot guarantee absolute prevention of criminal actions, it serves as a powerful deterrent and investigative tool. By strategically positioning cameras and integrating them with other security measures, businesses and property owners can significantly enhance their overall safety infrastructure. CCTV Monitoring Setup Guide: Secure Your Property Easily provides deeper insights into implementing an effective monitoring strategy tailored to specific security needs.
Types of CCTV Systems and Monitoring Methods
CCTV systems have evolved dramatically, transitioning from basic analogue setups to sophisticated digital surveillance networks. According to the National Protective Security Authority, modern Video Surveillance Systems (VSS) now operate over TCP/IP networks, offering significantly enhanced capabilities compared to traditional analogue installations. While analogue systems remain viable for smaller setups, digital technologies have revolutionised how we approach security monitoring.
Monitoring methods now encompass a range of sophisticated approaches. Wikipedia highlights the emergence of remote guarding – an advanced technique combining multiple technological elements. This approach integrates CCTV cameras with video analytics, alarm systems, dedicated monitoring centres, and trained security personnel, creating a comprehensive security ecosystem.
The primary types of CCTV systems include:
Here’s a comparison of the main types of CCTV systems and their key characteristics:
| Type of CCTV System | Connection Method | Key Advantages | Typical Use Cases |
|---|---|---|---|
| Analogue | Wired | Reliable Simple to install | Small shops Basic home security |
| Digital/IP | Network (TCP/IP) | High resolution Easy remote access | Large businesses Modern offices |
| Wireless | Wireless (Wi-Fi) | Flexible Easy to relocate | Temporary events Remote sites |
| Hybrid | Mixed (Wired & IP) | Versatile Supports upgrades | Expanding businesses Transition setups |
| Cloud-Based | Internet/Cloud | Off-site storage Accessible anywhere | Multi-site organisations Flexible operations |
- Analogue Systems: Traditional cameras with direct wired connections
- Digital/IP Systems: Network-based cameras with advanced data transmission
- Wireless Systems: Cameras operating without physical cable connections
- Hybrid Systems: Combining multiple technological approaches
- Cloud-Based Systems: Storing and accessing footage through online platforms
Modern monitoring strategies go beyond simple recording. They now feature intelligent capabilities like motion detection, facial recognition, and real-time threat assessment. Wireless CCTV Explained: Complete Guide for UK Security provides deeper insights into these cutting-edge surveillance technologies, helping businesses and property owners understand their comprehensive security options.
How CCTV Monitoring Works in Practice
CCTV monitoring is a sophisticated process that transforms raw video footage into actionable security intelligence. At its core, the system operates through a complex network of interconnected technologies designed to capture, analyse, and respond to potential security threats in real-time. Video surveillance goes far beyond simply recording images – it’s about creating an intelligent, proactive security ecosystem.
According to Wikipedia, remote guarding represents the pinnacle of modern monitoring techniques. This advanced approach integrates multiple technological components: CCTV cameras equipped with sophisticated video analytics, intelligent software algorithms, and dedicated monitoring centres staffed by trained security professionals. When cameras detect potential threats, the system immediately springs into action, with software conducting real-time event analysis and remote security officers prepared to take immediate intervention steps.
The practical monitoring process typically involves several key stages:
- Camera Capture: High-resolution cameras continuously record visual data
- Signal Transmission: Footage is transmitted via network or wireless connections
- Video Analytics: AI-powered software analyses the captured footage
- Threat Detection: Algorithms identify unusual or suspicious activities
- Human Verification: Trained security personnel review potential incidents
- Response Coordination: Appropriate actions are determined and executed
While technology plays a crucial role, human expertise remains fundamental to effective CCTV monitoring. CCTV Remote Viewing: Complete Guide for UK Businesses highlights how modern systems blend cutting-edge technology with professional human oversight, ensuring a comprehensive and responsive security approach that can adapt to complex real-world scenarios.
Legal Responsibilities and Data Protection UK
Navigating the legal landscape of CCTV monitoring in the United Kingdom requires a comprehensive understanding of complex data protection regulations. Surveillance legislation has evolved significantly, creating a robust framework that balances security needs with individual privacy rights. Property owners and businesses must carefully consider their legal obligations when implementing CCTV systems.
According to the UK Government, the Surveillance Camera Code of Practice – introduced under the Protection of Freedoms Act 2012 – provides critical guidelines for responsible CCTV operation. This legislation emphasizes the importance of accountability, ensuring that surveillance technologies are deployed with respect to civil liberties and individual privacy.
Key legal responsibilities for CCTV operators include:
- Lawful Purpose: Clearly defining and justifying the surveillance
- Data Minimization: Collecting only necessary visual information
- Storage Limitations: Implementing strict data retention protocols
- Individual Rights: Respecting subjects’ rights to access their recorded data
- Transparent Signage: Clearly indicating the presence of CCTV monitoring
- Secure Data Management: Protecting recorded footage from unauthorized access
For businesses and property managers seeking to understand the nuanced legal requirements, CCTV Regulations in Essex: Essential Guide provides comprehensive insights into navigating the complex regulatory environment. As the University of Derby highlights, recorded images are considered personal data under UK GDPR, mandating strict compliance with data protection principles of lawfulness, fairness, and transparency.
Common Mistakes and Security Vulnerabilities
CCTV systems are powerful security tools, but they are not infallible. Many organisations unknowingly compromise their security by falling into predictable traps that undermine the effectiveness of their surveillance infrastructure. Understanding these potential pitfalls is crucial for maintaining a robust security strategy.
According to the National Protective Security Authority, CCTV should never be viewed as a standalone solution. A critical mistake many make is over-relying on cameras without integrating them into a comprehensive security approach. This tunnel vision can create significant vulnerabilities, leaving critical gaps in protection that determined criminals could exploit.
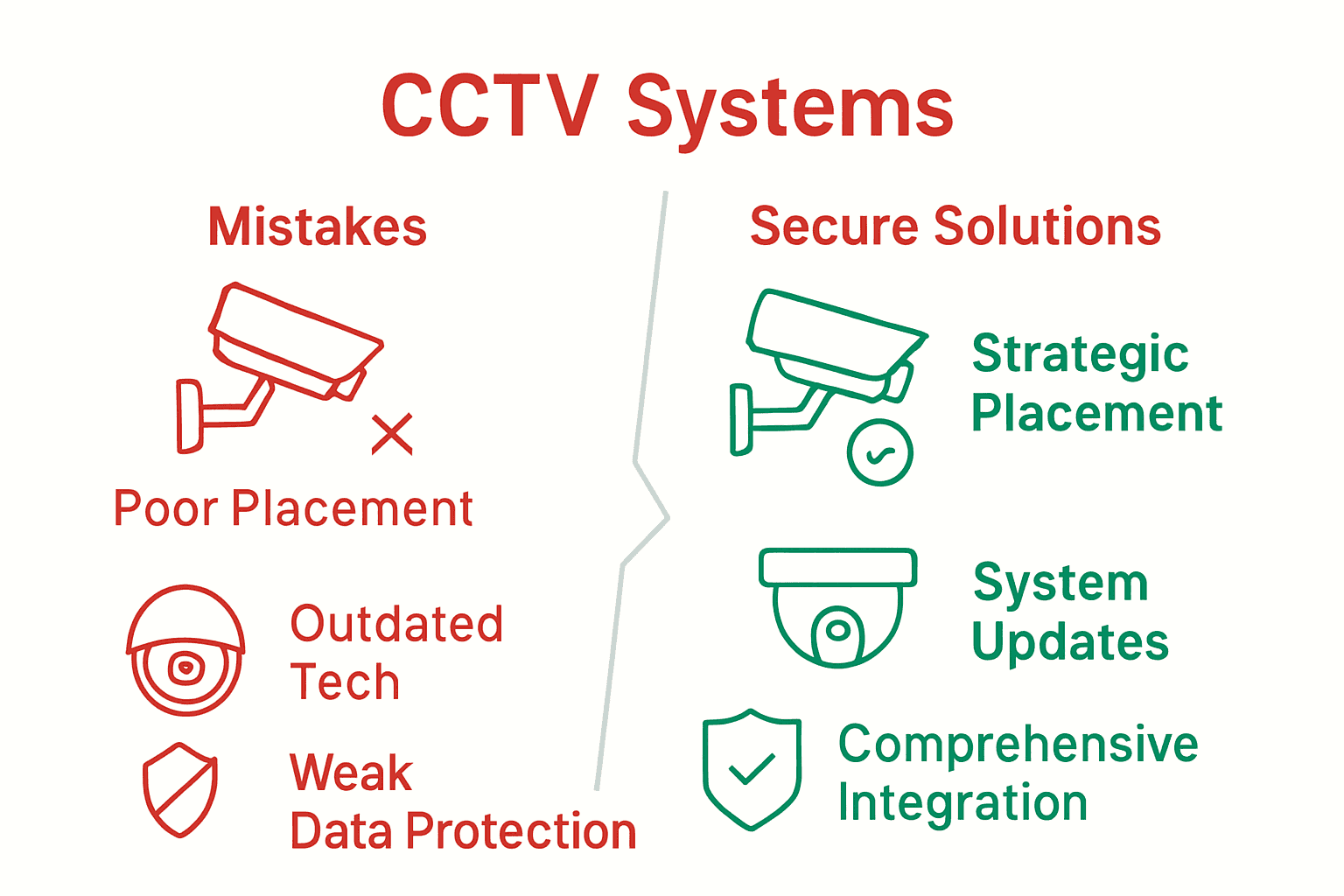
Common security vulnerabilities include:
- Poor Camera Placement: Leaving critical areas unmonitored
- Insufficient Data Protection: Vulnerable network configurations
- Outdated Technology: Using legacy systems with known security weaknesses
- Inadequate Staff Training: Improper monitoring and response protocols
- Limited Maintenance: Neglecting system updates and hardware checks
- Predictable Monitoring Patterns: Creating exploitable routines
Wikipedia highlights an innovative approach to mitigating these vulnerabilities: remote guarding. This method reduces false alarms by having trained agents carefully review each alert before taking action, significantly enhancing overall security effectiveness. Uncovering the Hidden Risks of Outdated Security Systems and How to Address Them provides deeper insights into identifying and addressing potential security system weaknesses.
Secure Your Property with Expert CCTV Monitoring Solutions
Understanding the crucial role of CCTV monitoring highlighted in the article reveals common challenges many property owners face today such as poor camera placement, outdated technology and the need for a comprehensive security approach beyond basic recording. Whether you want to deter crime effectively, ensure lawful data protection compliance or achieve real-time monitoring with professional support, the goal is clear: enhance your security with confidence and peace of mind.
Take control of your security today by choosing tailored CCTV installation and monitoring services from 247cctv.co.uk. Our expert team designs and installs advanced systems that integrate with burglar alarms and access control to give you a complete safety solution. Don’t wait until vulnerabilities are exploited. Explore our CCTV Monitoring Setup Guide: Secure Your Property Easily and learn how smart surveillance can protect your home or business. Ready to upgrade your security system smartly and legally? Visit 247cctv.co.uk now and get your personalised security assessment.
Frequently Asked Questions
What is the primary purpose of CCTV monitoring?
CCTV monitoring serves to enhance security by deterring criminal activities, providing visual evidence for investigations, and managing public order scenarios through real-time awareness and intervention capabilities.
How do different types of CCTV systems compare?
CCTV systems vary in connection methods and functionalities, including analogue systems for basic setups, digital/IP systems for high-resolution footage and easy access, wireless systems for flexibility, hybrid systems for versatility, and cloud-based systems for off-site storage and accessibility.
What are the key stages of CCTV monitoring in practice?
The monitoring process typically involves camera capture, signal transmission, video analytics for threat detection, human verification of incidents, and response coordination to address potential security threats.
What are common mistakes made when implementing CCTV systems?
Common mistakes include poor camera placement, insufficient data protection, using outdated technology, inadequate staff training, neglecting maintenance, and establishing predictable monitoring patterns that can be exploited by criminals.
Recommended
- Essential Guide to CCTV Installation in the UK – 247 CCTV Security Ltd
- CCTV Monitoring Setup Guide: Secure Your Property Easily – 247 CCTV Security Ltd
- CCTV Remote Viewing: Complete Guide for UK Businesses – 247 CCTV Security Ltd
- The Essential Guide to Home CCTV in the UK – 247 CCTV Security Ltd
- 5 Star CCTV Installation And Repair in Toronto

