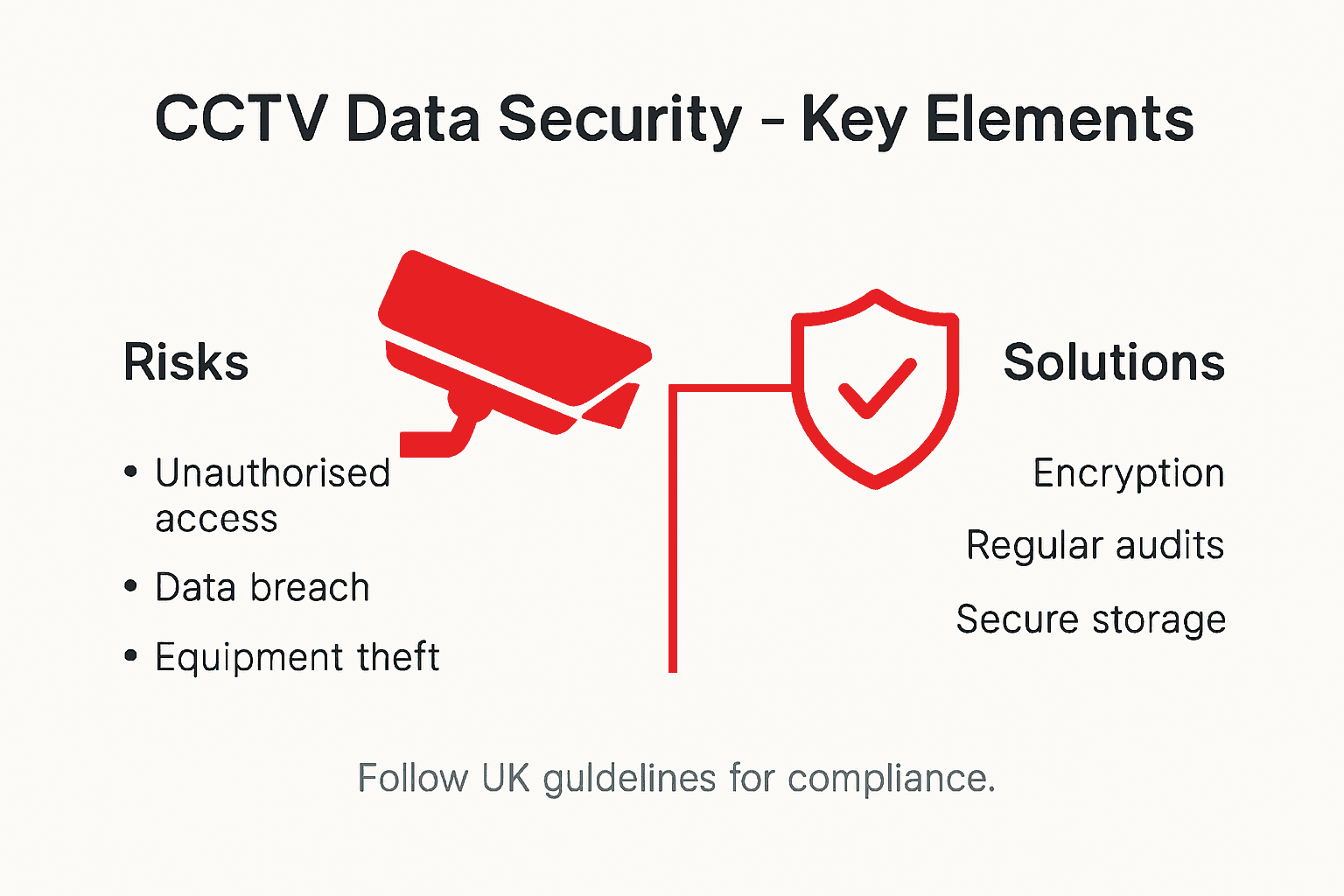
More than 70 percent of CCTV breaches in British commercial properties stem from weak data security protocols. For Facilities Managers in Essex, the stakes are higher as you safeguard sensitive footage while complying with strict UK privacy laws. Managing CCTV footage is not just about capturing incidents, it is about protecting every byte of data from unauthorized access and meeting rigorous British standards. This guide breaks down the concepts and practices that keep your surveillance footage secure and compliant.
Key Takeaways
| Point | Details |
|---|---|
| Data Security Principles | Emphasise the protection of information from unauthorised access, ensuring confidentiality, integrity, and availability within surveillance systems. |
| CCTV System Types | Different CCTV configurations present unique data security challenges, requiring tailored risk mitigation strategies for effective management. |
| Legal Compliance | Adhere to UK laws like the Data Protection Act 2018 and GDPR, ensuring lawful data processing, transparency, and respect for individual privacy rights. |
| Common Compliance Mistakes | Avoid pitfalls such as inadequate impact assessments and weak access controls by implementing stringent policies and regular audits. |
CCTV Data Security Explained – Key Concepts
Understanding data security in burglar alarm systems requires careful consideration of multiple protection layers. Modern security systems like the Hikvision AX Pro, RISCO LightSYS+, and Texecom Premier Elite integrate sophisticated data protection mechanisms to safeguard sensitive information collected during monitoring. These systems must comply with stringent UK regulatory standards that protect individual privacy while enabling effective security management.

The core principles of data security involve protecting information from unauthorised access, modification, or deletion. Government cyber security guidelines emphasise the critical need to maintain confidentiality, integrity, and availability of electronically stored data, particularly within surveillance and security infrastructure. For Facilities Managers, this means implementing robust access controls, encryption protocols, and comprehensive data retention policies that align with legal requirements.
Key data security strategies for burglar alarm systems include:
- Implementing role-based access controls
- Encrypting data during transmission and storage
- Regular security audits and vulnerability assessments
- Maintaining detailed access logs
- Securing network infrastructure against potential cyber threats
Pro tip: Conduct quarterly comprehensive security reviews of your alarm system’s data management practices to identify and mitigate potential vulnerabilities before they become significant risks.
Types Of CCTV Systems And Data Risks
Burglar alarm systems and CCTV technologies represent complex security infrastructures with diverse operational configurations and inherent data protection challenges. Different CCTV system types introduce unique data risk profiles that require nuanced understanding and strategic management, particularly for Facilities Managers responsible for comprehensive security oversight.
The primary CCTV system categories each present distinct data security considerations:
- Analogue Systems: Traditional camera setups with limited digital integration
- Digital IP Cameras: Network-connected systems enabling remote monitoring
- Cloud-Based Solutions: Centralised storage with advanced data management capabilities
- Wireless Systems: Mobile and flexible surveillance technologies
- Hybrid Configurations: Combining multiple technological approaches
Each system type demands specific risk mitigation strategies. Network-connected digital systems require robust cybersecurity protocols to prevent unauthorised data interception, while cloud-based solutions necessitate stringent encryption and access management. Comprehensive data protection impact assessments must evaluate camera placement, processing objectives, and potential privacy implications, ensuring compliance with UK data protection regulations.
The following table compares common CCTV system types and their primary data security challenges:
| System Type | Key Security Challenge | Typical Mitigation Approach |
|---|---|---|
| Analogue | Physical tampering risk | Secure housing and onsite access logs |
| Digital IP | Network interception | Encrypted transmission protocols |
| Cloud-Based | Third-party data exposure | Strong access controls, vendor audits |
| Wireless | Signal hijacking | Encrypted wireless communication |
| Hybrid | Complexity of mixed defences | Integrated layered security measures |
Pro tip: Develop a comprehensive data risk register that maps specific vulnerabilities across different CCTV system architectures, enabling proactive and targeted security management.
UK Laws Governing CCTV Data Protection
Facilities Managers must navigate a complex landscape of legal requirements governing CCTV data protection in the United Kingdom. The Data Protection Act 2018 and General Data Protection Regulation (GDPR) establish comprehensive legal frameworks that mandate rigorous standards for surveillance system management, requiring organisations to implement robust data handling protocols.
Key legislative provisions impacting CCTV data protection include:
- Requirement for lawful and transparent data processing
- Mandatory Data Protection Impact Assessments (DPIAs)
- Strict consent and privacy principles
- Limited data retention periods
- Fundamental rights of individuals to access and request data deletion
The National Surveillance Camera Strategy provides essential guidance for compliant CCTV operations across England and Wales, emphasising principles of proportionality, accountability, and transparency. Organisations must demonstrate they collect surveillance data only when absolutely necessary, with clear justification for each camera’s deployment and systematic documentation of processing activities.
Here is a summary of major UK CCTV legal requirements and their practical business implications:
| Legal Requirement | Practical Business Impact |
|---|---|
| Lawful data processing | Justify every camera and recording purpose |
| Data subject rights | Enable efficient access and deletion requests |
| Retention limitations | Implement clear deletion and retention policies |
| Mandatory DPIAs | Conduct and document impact assessments |
| Transparency and signage | Maintain visible explanation of surveillance use |
Pro tip: Maintain a comprehensive audit trail documenting every aspect of your CCTV data management strategy, ensuring demonstrable compliance with UK legal requirements.
Protocols For Storing And Accessing Footage
CCTV footage management requires meticulous attention to security, privacy, and legal compliance. Comprehensive data protection protocols mandate rigorous approaches to storing and controlling access to surveillance recordings, ensuring both organisational security and individual privacy rights.
Key protocols for secure footage management include:
- Encryption: Implementing robust encryption for all stored footage
- Access Controls: Establishing granular user permissions
- Audit Trails: Maintaining detailed logs of all access attempts
- Time-Limited Storage: Implementing automated deletion mechanisms
- Secure Storage Infrastructure: Using protected, segregated storage systems
Organisations must develop comprehensive governance frameworks that integrate technical controls with systematic documentation and monitoring processes, ensuring that access to sensitive surveillance data remains strictly controlled and accountable. This involves creating multilayered security mechanisms that prevent unauthorized viewing, copying, or manipulation of recorded material.
Pro tip: Conduct quarterly comprehensive access audits to verify that your CCTV footage management protocols remain robust, identifying and addressing any potential vulnerabilities in your security infrastructure.
Common Compliance Mistakes And How To Avoid Them
Surveillance data protection requires meticulous attention to prevent common compliance failures that can expose organisations to significant legal and financial risks. Facilities Managers must develop a proactive approach to identifying and mitigating potential regulatory breaches before they escalate.
Most prevalent compliance mistakes include:
- Inadequate Data Protection Impact Assessments (DPIAs)
- Poor Signage and Transparency
- Excessive Data Retention
- Weak Access Control Mechanisms
- Insufficient Staff Training
Comprehensive governance frameworks demand systematic interventions that address both technical and cultural aspects of data protection. This involves creating robust policies, conducting regular audits, and establishing clear accountability mechanisms that prevent unauthorized access and ensure ongoing compliance with UK data protection regulations.
Pro tip: Implement a mandatory quarterly compliance review process that systematically evaluates your CCTV data management practices, identifying potential vulnerabilities and ensuring continuous alignment with evolving regulatory requirements.
Secure Your CCTV Data with Expert Installation and Support
Facilities Managers face critical challenges protecting sensitive CCTV footage from unauthorised access and compliance risks. With increasing demands around encryption, lawful data processing, and robust access controls, it is essential to partner with trusted experts who understand UK regulations and implement cutting-edge security solutions such as role-based access and encrypted transmission protocols.
Enhance your building’s security infrastructure today by choosing 247 CCTV for professional CCTV, burglar alarm, and access control installations tailored to your needs. Our team ensures comprehensive data protection measures that align with the latest UK data security laws discussed in this article. Discover how our solutions deliver peace of mind and legal compliance. Visit our home page to get started and learn more about securing your surveillance systems with confidence.
Frequently Asked Questions
What are the core principles of data security in CCTV systems?
The core principles of data security in CCTV systems involve protecting information from unauthorised access, modification, or deletion, ensuring confidentiality, integrity, and availability of the data collected.
What are the key data security strategies that Facilities Managers should implement for CCTV systems?
Key strategies include implementing role-based access controls, encrypting data during transmission and storage, conducting regular security audits, maintaining access logs, and securing network infrastructure against cyber threats.
What legal requirements must Facilities Managers comply with regarding CCTV data protection?
Facilities Managers must comply with the Data Protection Act 2018 and GDPR, which mandate lawful data processing, Data Protection Impact Assessments (DPIAs), consent principles, limited data retention periods, and individual rights to access and delete data.
How can Facilities Managers secure access to CCTV footage and manage storage effectively?
Facilities Managers can secure access to CCTV footage by implementing encryption for stored footage, establishing granular access controls, maintaining audit trails, using time-limited storage, and ensuring secure storage infrastructure to prevent unauthorised access.
Recommended
- CCTV Network Security – Protecting Business and Home – 247 CCTV Security Ltd
- CCTV Regulations in Essex: Essential Guide – 247 CCTV Security Ltd
- Essential Guide to CCTV Installation in the UK – 247 CCTV Security Ltd
- Why Businesses Need CCTV: Complete Guide for 2025 – 247 CCTV Security Ltd
- Secure Removal Services Explained: Expert Guide for UK and North East Moves 2025 | Schott Removals
- Understanding Business Travel Safety Tips for Success

